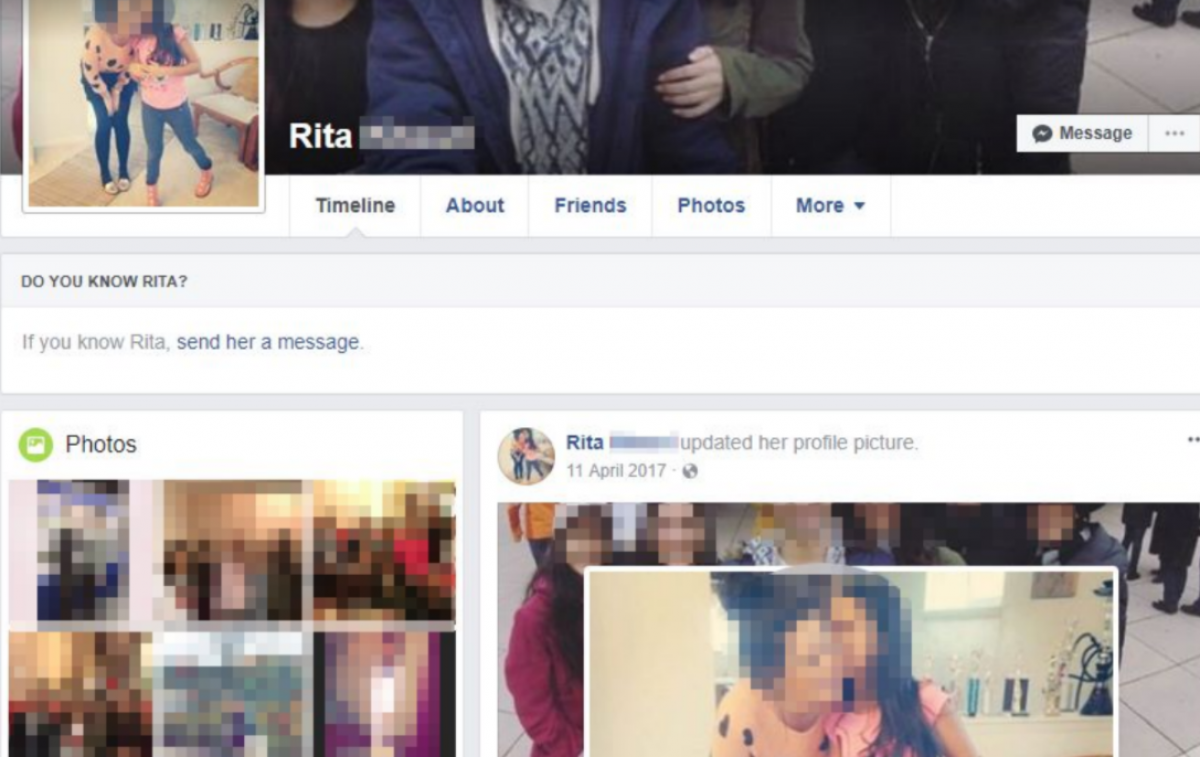
On Facebook, Rita, Alona and Christina appeared to be just like the millions of other U.S citizens sharing their lives with the world. They discussed family outings, shared emojis and commented on each other's photographs.
In reality, the three accounts were part of a highly-targeted cybercrime operation, used to spread malware that was able to steal passwords and spy on victims.
Hackers with links to Lebanon likely ran the covert scheme using a strain of malware dubbed "Tempting Cedar Spyware," according to researchers from Prague-based anti-virus company Avast, which detailed its findings in a report released on Wednesday.
In a honey trap tactic as old as time, the culprits' targets were mostly male, and lured by fake attractive women.
In the attack, hackers would send flirtatious messages using Facebook to the chosen victims, encouraging them to download a second, booby-trapped, chat application known as Kik Messenger to have "more secure" conversations. Upon analysis, Avast experts found that "many fell for the trap."
The Android spying malware was designed to steal data including contact lists, call logs, texts, photos, real-time geolocations and also record conversations. In short, it could transform a smartphone into the ultimate surveillance tool.
The victims of the operation had to adjust their device's security settings to install the fake Kik application from an unknown source, which should have raised red flags. But as Avast's researchers said in their report: sometimes temptation trumps security.
At least three Facebook accounts were found to have links to the spyware. They used the names Rita, Alona and Christina and photos stolen from real people. In a clear sign that it was a co-ordinated campaign, the profiles would interact.
Under a 'Family Day Out' update from Rita, Christina chimed in: "You guys look so cute lovely outfit." The reply read: "thank you darling" alongside a smiley emoji. They posted screenshots of a map claiming to be in San Francisco, California.
A Facebook search by Newsweek confirmed the accounts have been removed.
The majority of victims were based in the Middle East. While most were located in Israel, other targets were infected in the U.S, France, Germany and China.
Attackers' web addresses and working hours alluded to Lebanese involvement. As with all major cybercrime schemes, however, attribution remains difficult to prove with certainty. It appears the Tempting Cedar Spyware has been in use since 2015.
The fake profiles' Facebook "likes" were also worthy of attention, researchers said. In one example, they discovered Rita was interested in military groups including the U.S Army, the Israel Defense Forces (IDF) and the Lebanon & Israel Friendship Connection.
"Exceptionally dangerous"
"Despite unsophisticated techniques and the level of operational security being used, the attack managed to remain undetected for several years," Avast concluded.
"The cybercriminals behind the Tempting Cedar Spyware were able to install a persistent piece of spyware by exploiting social media, like Facebook, and people's lack of security awareness, and were thus able to gather sensitive and private data from their victims' phones including real-time location data which makes the malware exceptionally dangerous."
Last year, the Jerusalem Post revealed that a number of IDF soldiers had been compromised after being successfully targeted in a similar campaign. Using romantic lures, stolen pictures and chat apps, the hackers were allegedly linked to Hamas.
Uncommon Knowledge
Newsweek is committed to challenging conventional wisdom and finding connections in the search for common ground.
Newsweek is committed to challenging conventional wisdom and finding connections in the search for common ground.
About the writer
Jason Murdock is a staff reporter for Newsweek.
Based in London, Murdock previously covered cybersecurity for the International Business Times UK ... Read more
To read how Newsweek uses AI as a newsroom tool, Click here.