
Just weeks after releasing the details of 3,000 Brooklynites, a hacker collective aligned to the Islamic State militant group (ISIS) has disseminated another hit list among its supporters on the privacy app Telegram.
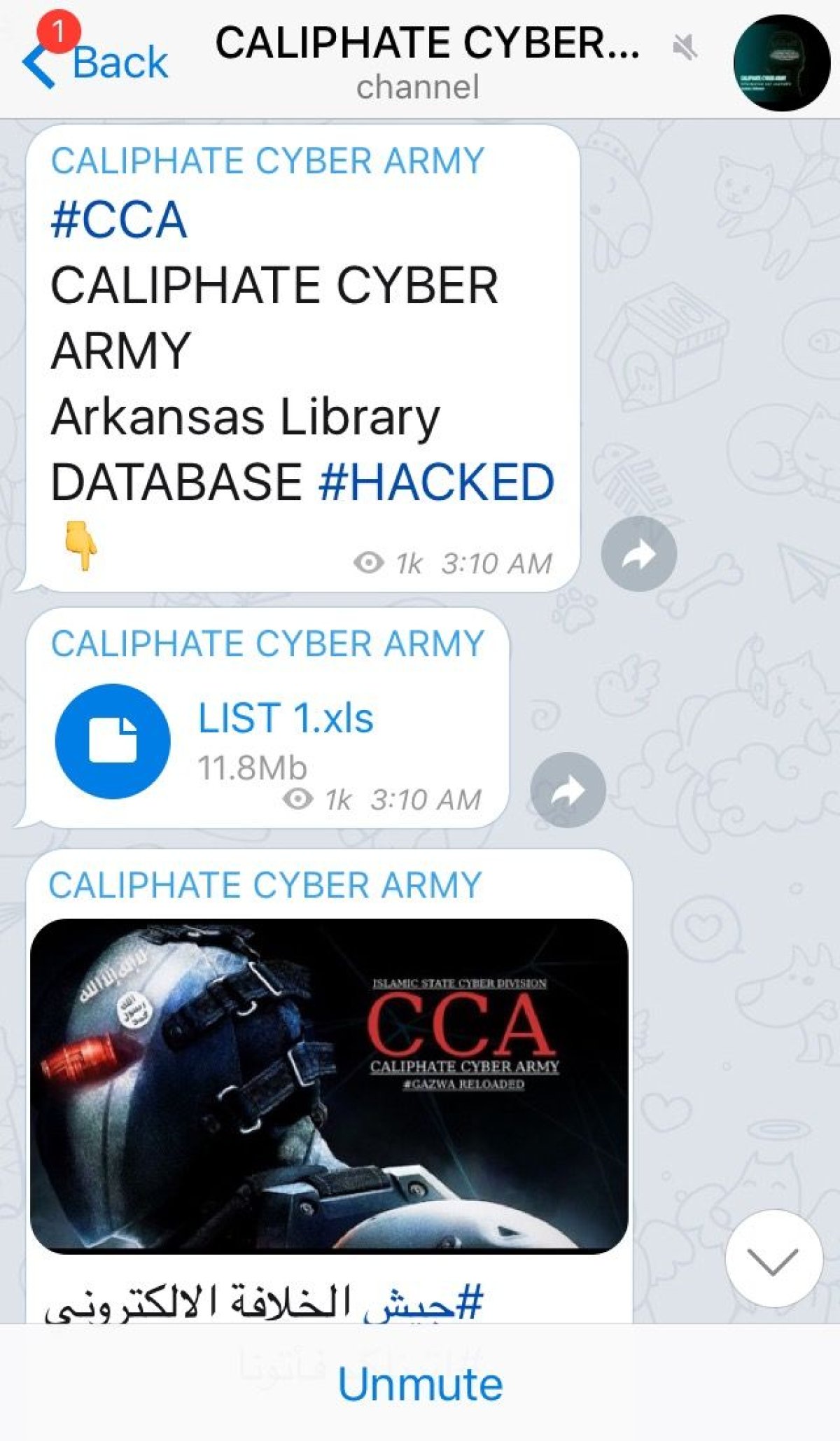
The 800 names did not originate from a prime U.S. metropolitan hub though, but the rural southeastern state of Arkansas. The target? The Arkansas Library Association.
ISIS released the identities of 800 library workers from backwater towns in Arkansas last month, as well as their addresses, email addresses and telephone numbers. A small prize for a radical Islamist group that has plotted large-scale attacks in capital cities to further its aim of striking fear into the heart of Western "crusaders," the association is as obscure as it is an obvious choice for ISIS to target.
The group's cyber-wing has initiated a trend of hacking low-level sites and databases, releasing civilian details in longer lists with increasing frequency. It had previously released the details of military, governmental or diplomatic personnel. It is a key tenet of the group's amateurish cyber strategy of damaging Western interests and affecting civilians in areas of the Western world that the group is unable to reach.
ISIS publishes the lists and calls upon its supporters, more lone wolves than organized cells, to target those named in the list's home country. In the instance of the New York hit list, the NYPD or the FBI visited members to notify them and offer security advice.
But this latest hit list has left security services and members of this particular database breach unmoved. The group's limited success on the battlefield in its self-proclaimed caliphate in Iraq and Syria is being reflected in cyberspace. The Arkansas State Police is not working on the case and is leaving the follow-up to the Arkansas Library Association.
Bill Sadler, spokesperson for the Arkansas State Police, tells Newsweek : "All I can tell you is that the Arkansas State Police is aware of the breach of the server. The Arkansas police does not have an open investigation and, as far as any notifications, that would be within the purview of the agency who lost the data."
Instead of visits or direct contact to those on the list, the FBI chose to inform the Arkansas Library Association who would then contact those named. State and federal authorities essentially left the association to its own devices to inform the 800 people of the database hack, according to an email sent to members and obtained by Newsweek. No security advice was offered to the members of the association by the FBI nor the association itself.
"Just wanted to let you know that the FBI informed that the data that was stolen from us has appeared on a pro-ISIL website," the email from the association's webmaster to its members read, using an acronym for ISIS.
"This data is basically, names, addresses, and phone numbers. We have cooperated with the authorities and we hope that this helps in catching the perpetrators of this hack. Sorry to have to report this, but I thought you'd rather know from us directly, rather than hear from a third party."
It appears that the FBI does not believe the threat from ISIS's cyber-hacks and lone-wolf directives is serious enough to occupy its resources on each individual. The agency told Newsweek in a statement that while its practise is to not comment on matters pertaining to an investigation, it "routinely notifies individuals and organizations of information collected… that may be perceived as potentially threatening in nature." It added that such information is shared to "sensitize potential victims to the observed threat, and to assist them in taking proper steps to ensure their safety."
While the federal agency notified the Arkansas Library Association, the absence of serious advice shows that ISIS's scare tactic is not having its desired effect. This relaxed, almost unconcerned, approach is shared by those on the list.
A library director from a small town in Arkansas on the list, who requested that his name be withheld for security reasons, says that those on the list were more relieved that their financial details were not released, as opposed to their personal details, adding that his colleagues were "by and large not too concerned" and he had found it "vaguely amusing."
"We're not at all concerned because we don't believe that there's any likelihood of anybody attacking us or anything of that sort. More than anything else, we are puzzled as to how on earth they were even aware of our association's existence," he says.
"We're an obscure state library association and we just wouldn't think that we would be on anybody's radar. Our credit card information didn't get stolen apparently so we're glad for that. I think that's what we're worried about more than anything else."
While the Arkansas members of this list may be perplexed, this strategy of targeting random websites is one that the group's hackers have embarked on since the beginning of 2015. They have hit the wrong Google, Newsweek's Twitter account, a Michigan church and a small U.K. solar energy firm.
"They are clearly looking for low-hanging fruit, and, evidently, security features of this library's website are not up to par," says Michael Smith, an adviser to the U.S. congress and co-founder of national security firm Kronos Advisory.
"This fits with a pattern of targeting websites with weak security," he adds. "In most cases, hackers claiming affiliation with the Islamic State have targeted obscure websites."
Security experts say this tactic is not having its desired impact, with civilians and security services not stirred into action or fear, as more names means less of a threat.
"If you've got another 800 people from the Arkansas library, well, so what? The more names you get put out there, the less sort of threat there is," says Richard Barrett, the former head of Britain's MI6 global counter-extremism arm. "Being on the back foot, they need to show that they can project their power more broadly. But to just have a great blast of names, I don't that that's a very effective way of targeting."
ISIS's fundamental message remains that of attack you who can, where you can and when you can in the lands of the "kuffar," or infidels, demonstrating a lack of infrastructure, adds Barrett. This strategy is one that ISIS's main spokesperson and director of the group's external operations, Abu Mohammed al-Adnani, has pushed, calling for ISIS sympathizers to launch individual attacks in their home countries to kill Westerners "in any manner or way, however it may be."
Even if this tactic does spark a sense of "terror" in members of these hit lists, its fear factor is limited, says Barrett, using the deadly Paris attacks in November 2015 or the Brussels attacks in March as examples of where jihadis have garnered a more fearful reaction from a larger number of people in Europe's major cities.
"[The members of these lists] do not know what it means. They may think that there are secret armies just waiting for directions," he says. "I don't think the security services would take them very seriously. You're scaring a few named people, rather than the mass of the population."
Max Kutner contributed reporting on this article.
Uncommon Knowledge
Newsweek is committed to challenging conventional wisdom and finding connections in the search for common ground.
Newsweek is committed to challenging conventional wisdom and finding connections in the search for common ground.
About the writer
Jack is International Security and Terrorism Correspondent for Newsweek.
Email: j.moore@newsweek.com
Encrypted email: jfxm@protonmail.com
Available on Whatsapp, Signal, Wickr, Telegram, Viber.
Twitter: @JFXM
Instagram: Read more
To read how Newsweek uses AI as a newsroom tool, Click here.








